mirror of
https://github.com/callebtc/electronwall.git
synced 2025-12-18 07:34:19 +01:00
rename list
This commit is contained in:
@@ -1,5 +1,5 @@
|
||||
# ⚡️🛡 electronwall
|
||||
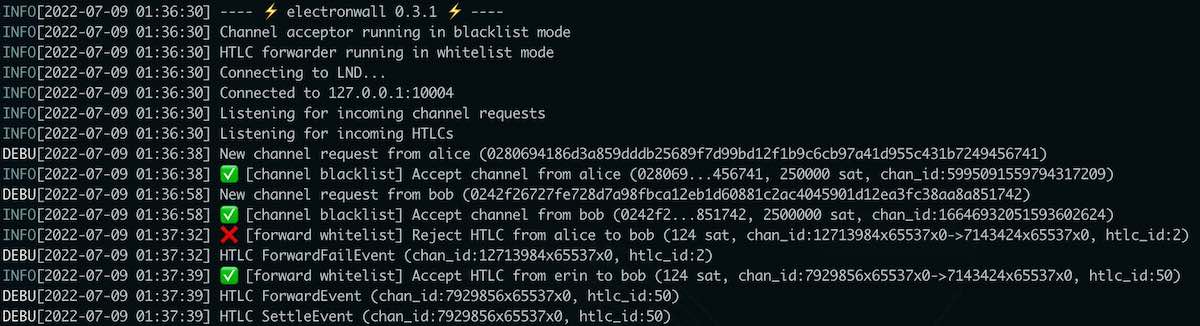
A tiny firewall for LND that can filter Lightning channel opening requests and HTLC forwards on your node. electronwall runs in the background and either allows (whitelist) or rejects (blacklist) events from a list of node public keys for channel openings, or channel IDs and channel pairs for payment routings.
|
||||
A tiny firewall for LND that can filter Lightning channel opening requests and HTLC forwards on your node. electronwall runs in the background and either allows (allowlist) or rejects (denylist) events from a list of node public keys for channel openings, or channel IDs and channel pairs for payment routings.
|
||||
|
||||
|
||||
|
||||
|
||||
@@ -44,17 +44,17 @@ func (app *app) dispatchChannelAcceptor(ctx context.Context) {
|
||||
|
||||
var accept bool
|
||||
|
||||
if Configuration.ChannelMode == "whitelist" {
|
||||
if Configuration.ChannelMode == "allowlist" {
|
||||
accept = false
|
||||
for _, pubkey := range Configuration.ChannelWhitelist {
|
||||
for _, pubkey := range Configuration.ChannelAllowlist {
|
||||
if hex.EncodeToString(req.NodePubkey) == pubkey {
|
||||
accept = true
|
||||
break
|
||||
}
|
||||
}
|
||||
} else if Configuration.ChannelMode == "blacklist" {
|
||||
} else if Configuration.ChannelMode == "denylist" {
|
||||
accept = true
|
||||
for _, pubkey := range Configuration.ChannelBlacklist {
|
||||
for _, pubkey := range Configuration.ChannelDenylist {
|
||||
if hex.EncodeToString(req.NodePubkey) == pubkey {
|
||||
accept = false
|
||||
break
|
||||
|
||||
20
config.go
20
config.go
@@ -13,12 +13,12 @@ var Configuration = struct {
|
||||
MacaroonPath string `yaml:"macaroon_path"`
|
||||
TLSPath string `yaml:"tls-path"`
|
||||
Debug bool `yaml:"debug"`
|
||||
ChannelWhitelist []string `yaml:"channel-whitelist"`
|
||||
ChannelBlacklist []string `yaml:"channel-blacklist"`
|
||||
ChannelAllowlist []string `yaml:"channel-allowlist"`
|
||||
ChannelDenylist []string `yaml:"channel-denylist"`
|
||||
ChannelRejectMessage string `yaml:"channel-reject-message"`
|
||||
ForwardMode string `yaml:"forward-mode"`
|
||||
ForwardWhitelist []string `yaml:"forward-whitelist"`
|
||||
ForwardBlacklist []string `yaml:"forward-blacklist"`
|
||||
ForwardAllowlist []string `yaml:"forward-allowlist"`
|
||||
ForwardDenylist []string `yaml:"forward-denylist"`
|
||||
}{}
|
||||
|
||||
func init() {
|
||||
@@ -49,19 +49,19 @@ func checkConfig() {
|
||||
}
|
||||
|
||||
if len(Configuration.ChannelMode) == 0 {
|
||||
Configuration.ChannelMode = "blacklist"
|
||||
Configuration.ChannelMode = "denylist"
|
||||
}
|
||||
if Configuration.ChannelMode != "whitelist" && Configuration.ChannelMode != "blacklist" {
|
||||
panic(fmt.Errorf("channel mode must be either whitelist or blacklist"))
|
||||
if Configuration.ChannelMode != "allowlist" && Configuration.ChannelMode != "denylist" {
|
||||
panic(fmt.Errorf("channel mode must be either allowlist or denylist"))
|
||||
}
|
||||
|
||||
log.Infof("Channel acceptor running in %s mode", Configuration.ChannelMode)
|
||||
|
||||
if len(Configuration.ForwardMode) == 0 {
|
||||
Configuration.ForwardMode = "blacklist"
|
||||
Configuration.ForwardMode = "denylist"
|
||||
}
|
||||
if Configuration.ForwardMode != "whitelist" && Configuration.ForwardMode != "blacklist" {
|
||||
panic(fmt.Errorf("channel mode must be either whitelist or blacklist"))
|
||||
if Configuration.ForwardMode != "allowlist" && Configuration.ForwardMode != "denylist" {
|
||||
panic(fmt.Errorf("channel mode must be either allowlist or denylist"))
|
||||
}
|
||||
|
||||
log.Infof("HTLC forwarder running in %s mode", Configuration.ForwardMode)
|
||||
|
||||
@@ -10,28 +10,28 @@ debug: true
|
||||
|
||||
# ----- Channel openings -----
|
||||
|
||||
# Mode can either be "blacklist" or "whitelist"
|
||||
channel-mode: "blacklist"
|
||||
# Mode can either be "denylist" or "allowlist"
|
||||
channel-mode: "denylist"
|
||||
|
||||
# This error message will be sent to the other party upon a reject
|
||||
channel-reject-message: "Contact me at user@email.com"
|
||||
|
||||
# List of nodes to whitelist or blacklist
|
||||
channel-whitelist:
|
||||
# List of nodes to allowlist or denylist
|
||||
channel-allowlist:
|
||||
- "03de70865239e99460041e127647b37101b9eb335b3c22de95c944671f0dabc2d0"
|
||||
- "0307299a290529c5ccb3a5e3bd2eb504daf64cc65c6d65b582c01cbd7e5ede14b6"
|
||||
channel-blacklist:
|
||||
channel-denylist:
|
||||
- "02853f9c1d15d479b433039885373b681683b84bb73e86dff861bee6697c17c1de"
|
||||
|
||||
# ----- HTLC forwarding -----
|
||||
|
||||
# Mode can either be "blacklist" or "whitelist"
|
||||
forward-mode: "blacklist"
|
||||
# Mode can either be "denylist" or "allowlist"
|
||||
forward-mode: "denylist"
|
||||
|
||||
# List of channel IDs to whitelist or blacklist
|
||||
forward-whitelist:
|
||||
# List of channel IDs to allowlist or denylist
|
||||
forward-allowlist:
|
||||
- "7143424x65537x0"
|
||||
- "12320768x65536x0->7143424x65537x0"
|
||||
forward-blacklist:
|
||||
forward-denylist:
|
||||
- "12320768x65536x0"
|
||||
- "7929856x65537x1->12320768x65536x0"
|
||||
|
||||
@@ -154,19 +154,23 @@ func (app *app) interceptHtlcEvents(ctx context.Context, interceptor routerrpc.R
|
||||
// decision is made whether or not to relay an HTLC to the next
|
||||
// peer.
|
||||
// The decision is made based on the following rules:
|
||||
// 1. Either use a whitelist (accept) or a blacklist (deny).
|
||||
// 1. Either use a allowlist or a denylist.
|
||||
// 2. If a single channel ID is used (12320768x65536x0), check the incoming ID of the HTLC against the list.
|
||||
// 3. If two channel IDs are used (7929856x65537x0->7143424x65537x0), check the incoming ID and the outgoing ID of the HTLC against the list.
|
||||
func (app *app) htlcInterceptDecision(ctx context.Context, event *routerrpc.ForwardHtlcInterceptRequest, decision_chan chan bool) {
|
||||
var accept bool
|
||||
|
||||
// sleep for 10 seconds
|
||||
log.Infof("Sleeping for 15 seconds")
|
||||
time.Sleep(15 * time.Second)
|
||||
|
||||
switch Configuration.ForwardMode {
|
||||
case "whitelist":
|
||||
case "allowlist":
|
||||
accept = false
|
||||
for _, forward_whitelist_entry := range Configuration.ForwardWhitelist {
|
||||
if len(strings.Split(forward_whitelist_entry, "->")) == 2 {
|
||||
for _, forward_allowlist_entry := range Configuration.ForwardAllowlist {
|
||||
if len(strings.Split(forward_allowlist_entry, "->")) == 2 {
|
||||
// check if channel_id is actually from-to channel
|
||||
split := strings.Split(forward_whitelist_entry, "->")
|
||||
split := strings.Split(forward_allowlist_entry, "->")
|
||||
from_channel_id, to_channel_id := split[0], split[1]
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == from_channel_id &&
|
||||
parse_channelID(event.OutgoingRequestedChanId) == to_channel_id {
|
||||
@@ -175,18 +179,18 @@ func (app *app) htlcInterceptDecision(ctx context.Context, event *routerrpc.Forw
|
||||
}
|
||||
} else {
|
||||
// single entry
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == forward_whitelist_entry {
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == forward_allowlist_entry {
|
||||
accept = true
|
||||
break
|
||||
}
|
||||
}
|
||||
}
|
||||
case "blacklist":
|
||||
case "denylist":
|
||||
accept = true
|
||||
for _, forward_whitelist_entry := range Configuration.ForwardWhitelist {
|
||||
if len(strings.Split(forward_whitelist_entry, "->")) == 2 {
|
||||
for _, forward_allowlist_entry := range Configuration.ForwardAllowlist {
|
||||
if len(strings.Split(forward_allowlist_entry, "->")) == 2 {
|
||||
// check if channel_id is actually from-to channel
|
||||
split := strings.Split(forward_whitelist_entry, "->")
|
||||
split := strings.Split(forward_allowlist_entry, "->")
|
||||
from_channel_id, to_channel_id := split[0], split[1]
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == from_channel_id &&
|
||||
parse_channelID(event.OutgoingRequestedChanId) == to_channel_id {
|
||||
@@ -195,7 +199,7 @@ func (app *app) htlcInterceptDecision(ctx context.Context, event *routerrpc.Forw
|
||||
}
|
||||
} else {
|
||||
// single entry
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == forward_whitelist_entry {
|
||||
if parse_channelID(event.IncomingCircuitKey.ChanId) == forward_allowlist_entry {
|
||||
accept = false
|
||||
break
|
||||
}
|
||||
|
||||
Reference in New Issue
Block a user